8kSec FridaInTheMiddle¶
Description: Welcome to FridaInTheMiddle, a Swift-based iOS application that’s extremely sensitive to uninvited interference. It comes equipped with active runtime tamper detection that watches for signs of Frida, whether through suspicious ports, injected dylibs, or unauthorized hooks.
Link: https://academy.8ksec.io/course/ios-application-exploitation-challenges
Install an IPA file can be difficult. So, for make it more easy, I made a YouTube video with the process using Sideloadly. LINK: https://www.youtube.com/watch?v=YPpo9owRKGE
Once you have the app installed, let's proceed with the challenge. unzip the .ipa file.
Recon¶
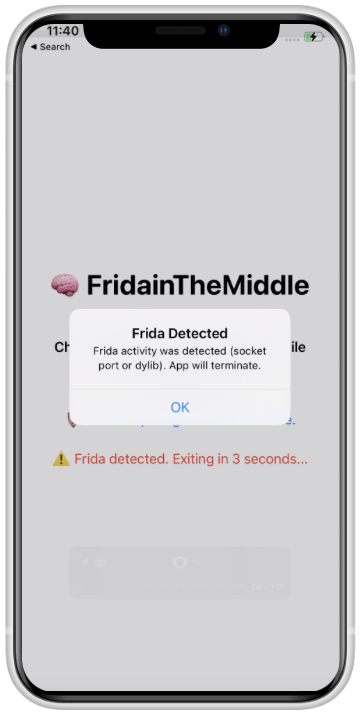
If we launch the app, this will be closed.
This means the app detects if we run Frida even without spawning it or anything. Something we can use to our advantage.
In fact, the error message shows that it is detected due to the socket port or a dylib.
So, may be we need rename the FridaGadget.dylib?
Or just rename the frida-server binary, and then, launch it with another port?
Let's try it!
Bypass¶
Login via SSH to your iPhone with jailbreak.
First, kill the frida-server:
system-8ksec (server) in some random port: The default port is 27042. Now, if we spawn the app using Frida, we can see that we already bypass it!
Notice that the Intercept First Argument Using Frida text is a button!
Getting the Flag¶
Finally, we have the hint that the flag function is called dummyFunction.
So, we can enumerate the loaded modules and functions.
Also, try to hook them!
But first, let's make a search:
Process.enumerateModules().forEach(mod => {
if (mod.name.includes("FridaInTheMiddle")) {
console.log("module:", mod.name);
mod.enumerateSymbols().forEach(sym => {
if (sym.name.includes("dummyFunction") && sym.name.includes("flag")) {
console.log("--", sym.name, "@", sym.address);
}
});
}
});
module: FridaInTheMiddle
module: FridaInTheMiddle.debug.dylib
-- $s16FridaInTheMiddle11ContentViewV13dummyFunction4flagySS_tF @ 0x1003c5d24
-- $s16FridaInTheMiddle11ContentViewV13dummyFunction4flagySS_tF @ 0x1003c5d24
Now, let's try call the function!
For that, I made this script
// search symbol
function findDummy() {
var found = null;
Process.enumerateModules().forEach(function(mod) {
if (mod.name.includes("FridaInTheMiddle")) {
mod.enumerateSymbols().forEach(function(sym) {
if (sym.name.includes("dummyFunction")) {
found = sym;
console.log("found:", sym.name, "at", sym.address);
}
});
}
});
return found;
}
// try hook
function tryHook() {
var sym = findDummy();
if (sym) {
console.log('hooking:', sym.name);
Interceptor.attach(sym.address, {
onEnter(args) {
console.log('dummyFunction called!');
console.log('Args:', args[0], args[1], args[2]);
console.log(hexdump(args[1], {length: 64}));
}
});
return true;
}
return false;
}
tryHook();
Dynamically locates the dummyFunction symbol inside the target module and hooks it. When the function is triggered, it logs the arguments and dumps memory from the second argument, which contains the flag.
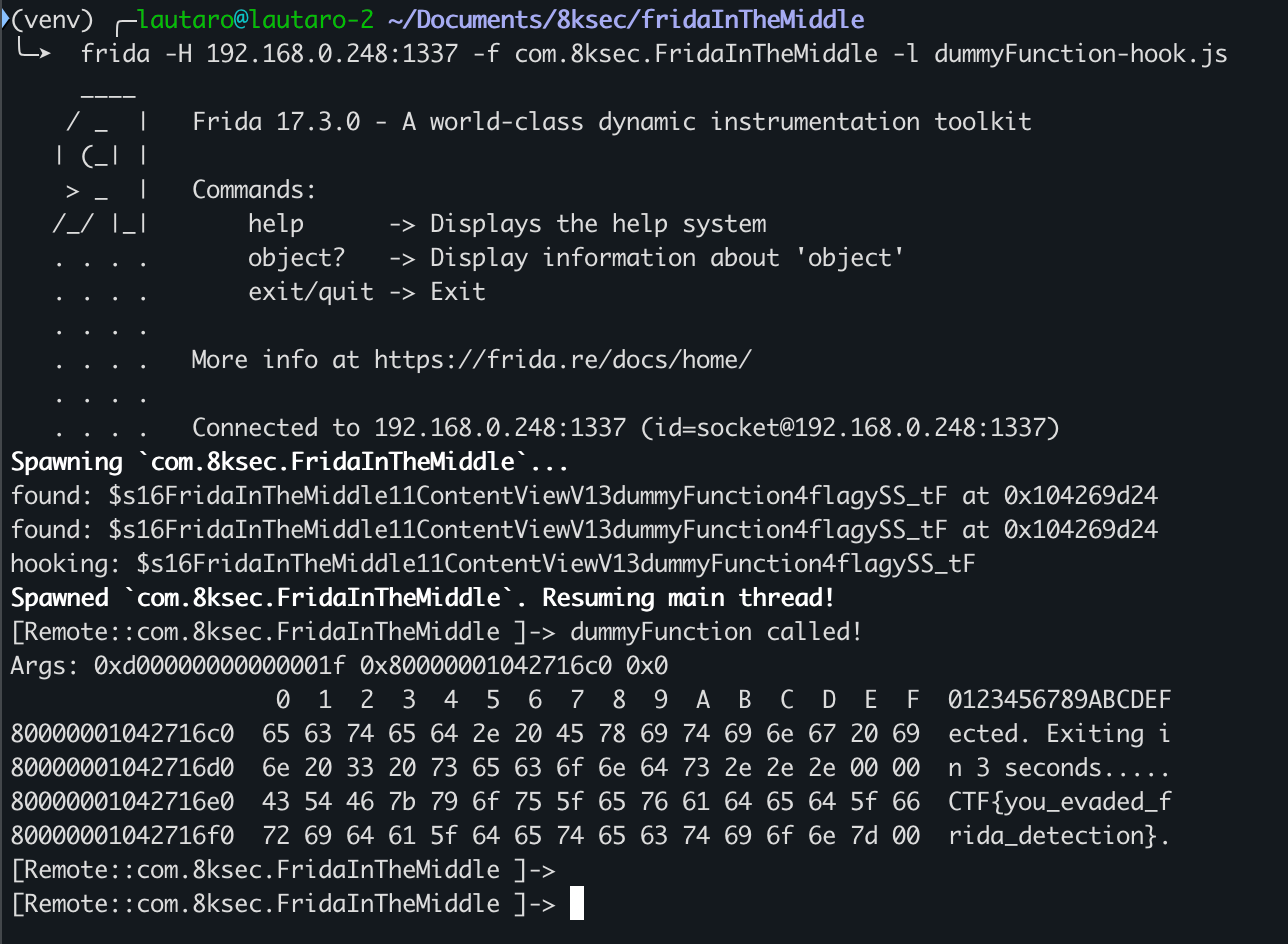
Finally, run the Frida command:
Output: ____
/ _ | Frida 17.3.0 - A world-class dynamic instrumentation toolkit
| (_| |
> _ | Commands:
/_/ |_| help -> Displays the help system
. . . . object? -> Display information about 'object'
. . . . exit/quit -> Exit
. . . .
. . . . More info at https://frida.re/docs/home/
. . . .
. . . . Connected to 192.168.0.248:1337 (id=socket@192.168.0.248:1337)
Spawning `com.8ksec.FridaInTheMiddle`...
found: $s16FridaInTheMiddle11ContentViewV13dummyFunction4flagySS_tF at 0x104269d24
found: $s16FridaInTheMiddle11ContentViewV13dummyFunction4flagySS_tF at 0x104269d24
hooking: $s16FridaInTheMiddle11ContentViewV13dummyFunction4flagySS_tF
Spawned `com.8ksec.FridaInTheMiddle`. Resuming main thread!
[Remote::com.8ksec.FridaInTheMiddle ]->
Just press the text mentioned previously (launch the dummyFunction) and you will see the flag!
Flag: CTF{you_evaded_frida_detection}
I hope you found it useful (: